- Support portal
- Evaluation Kits and partner products
u-blox Support
- Product documentation
Documentation
- Investor relations
Investor relations
Guest blogs
|
07 Apr 2017
Security gets FASTR for automotive

In a connected world, very few worthwhile things can happen in isolation, and this is particularly true of automotive security and privacy. That’s why the Future of Automotive Security Technology Research (FASTRSM) consortium recently released a very formal and detailed manifesto, and with it, a call-to-action to the entire automotive supply chain.
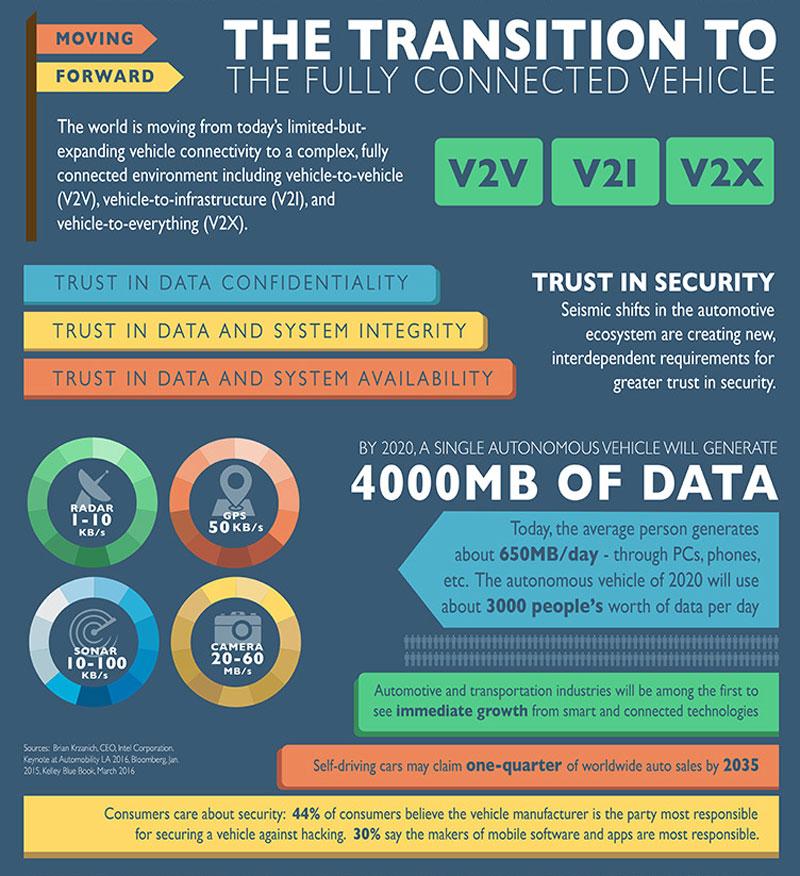
The big driver for security (pardon the pun) is the escalating level of communications, both between modules in the vehicle itself, as well as vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I) and vehicle-to-everything (V2X). The big realization, of course, is that we’re rapidly tumbling towards rising levels of vehicle autonomy that, according to FASTR, will be generating somewhere in the region of 4 gigabytes per vehicle by 2020 (Figure 1). While this is technologically exciting, it’s also terrifying from a security, privacy, user trust and liability point of view.

Figure 1: FASTR recognizes that the transition to higher levels of V2I, V2V, and V2X communication and autonomy creates more data and privacy concerns, which users will look to the industry to solve. (Image source: FASTR consortium)
That fear is well-founded. To prove the point, researchers hacked a Jeep to expose vulnerabilities, and have continued to do so even after the initial vulnerability was shut down by Chrysler.
However, for anyone familiar with electronic systems, software and user habits, security will always be a moving target, kind of like cybersecurity “whack-a-mole”. If one attack surface gets shut down, hackers move on to another. If the car manufacturer chooses to do over-the-air (OTA) updates to close the vulnerability, that OTA connection becomes a hacker target: sending a USB stick with self-installing firmware updates to the user, or doing updates only in secure locations by the car dealer, is often the best solution.
Even then, with all the hardware, software, and connectivity loopholes closed, the user themselves can be tricked into giving away access codes, if the hackers are that intent on gaining access. Unless it’s a targeted attack for specific purposes, hackers, fortunately, are still human: they’ll move on to an easier target, we hope.
However, in an era of heightened security and privacy concerns, few want to rely upon hope as a solution, particularly anyone who might be in a position to be targeted. And vehicle manufacturers would rather avoid the publicity.
This brings us to FASTR and its manifesto. FASTR was founded in 2016 by Aeries, Intel, and Uber as a means of working with the expanding automotive ecosystem to accelerate the realization of organically secure vehicles. Along with the new manifesto announced in February, FASTR also welcomed Karamba Security and Rambus to the consortium.
Given the scope of the issue, a concerted effort is clearly necessary: 250 million connected vehicles will be on roadways by 2020 and the expected market for autonomous vehicles looks likely to approach $77 billion in 2023. FASTR itself pointed to some of the potential attack surfaces (Figure 2).
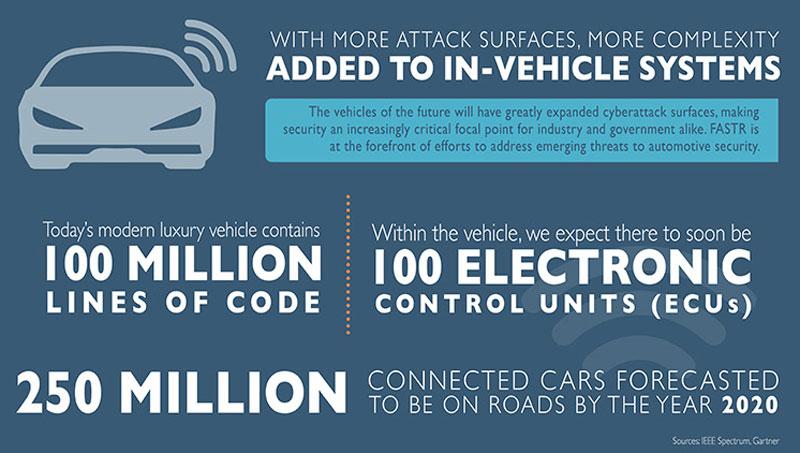
Figure 2: The lines of code and the attack surfaces on a connected vehicle are going to grow rapidly as we accelerate toward more connected vehicles with higher levels of autonomy. Collaboration through FASTR might be a good idea. (Image source: FASTR consortium)
It isn’t just the electronic control units (ECUs) deep within the vehicle itself that can be dangerous if hacked. Remotely cranking the entertainment unit may seem like harmless fun for tricksters, but it can kill if the driver is distracted or surprised at the wrong time.
For sure, black-hat-turned-white-hat operators are now being gainfully employed to ensure security, and the vulnerabilities are being addressed. User access is gated by biometrics, dual-authentication methods and even the old passwords. Communication gateways can be used to provide domain isolation, as well as encrypted data, while processors and software are becoming more tamper-proof.
Still, a cohesive approach across the whole industry that addresses the following has not been forthcoming:
The FASTR consortium is gathering together OEMs, transportation network companies, supply-chain providers (Tier 1s and 2s), autonomous vehicle specialists, integrated circuit (IC) suppliers, specialists in automotive security, academics and researchers. As a collaborative effort, it hopes to address security from top to bottom, including:
Security in a vacuum is easy, but security in the real world across a vast ecosystem takes collaboration at an unprecedented level. While we don’t suggest cloaking vehicles in aluminum foil (yet), awareness of the issues and working with a knowledgeable partner or two are good starting points.